Divine Info About How To Detect Conficker C

In order to make absolutely sure that conficker.c has not affected your computer, you have the following options:
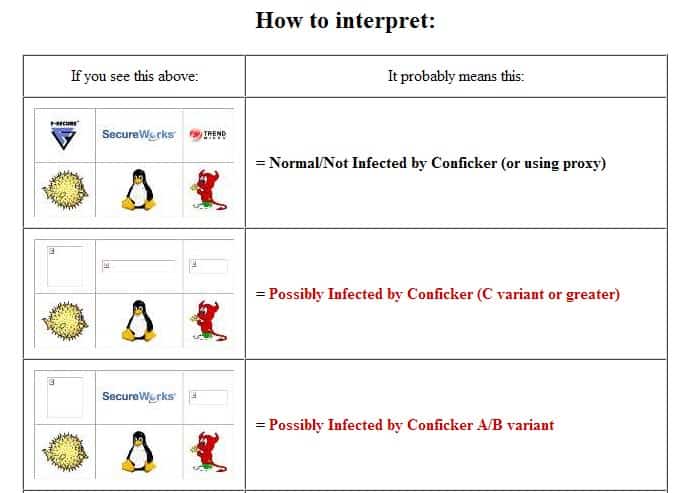
How to detect conficker c. The latest version of nmap has the ability to detect all (current) variants of conficker by detecting the otherwise almost invisible changes that the worm makes to the port 139 and port 445. Pass the flow record if the. In the add a file or folder dialog box, browse to the.
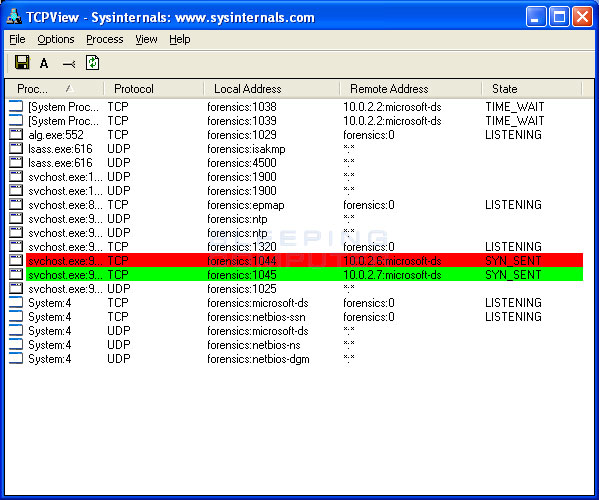
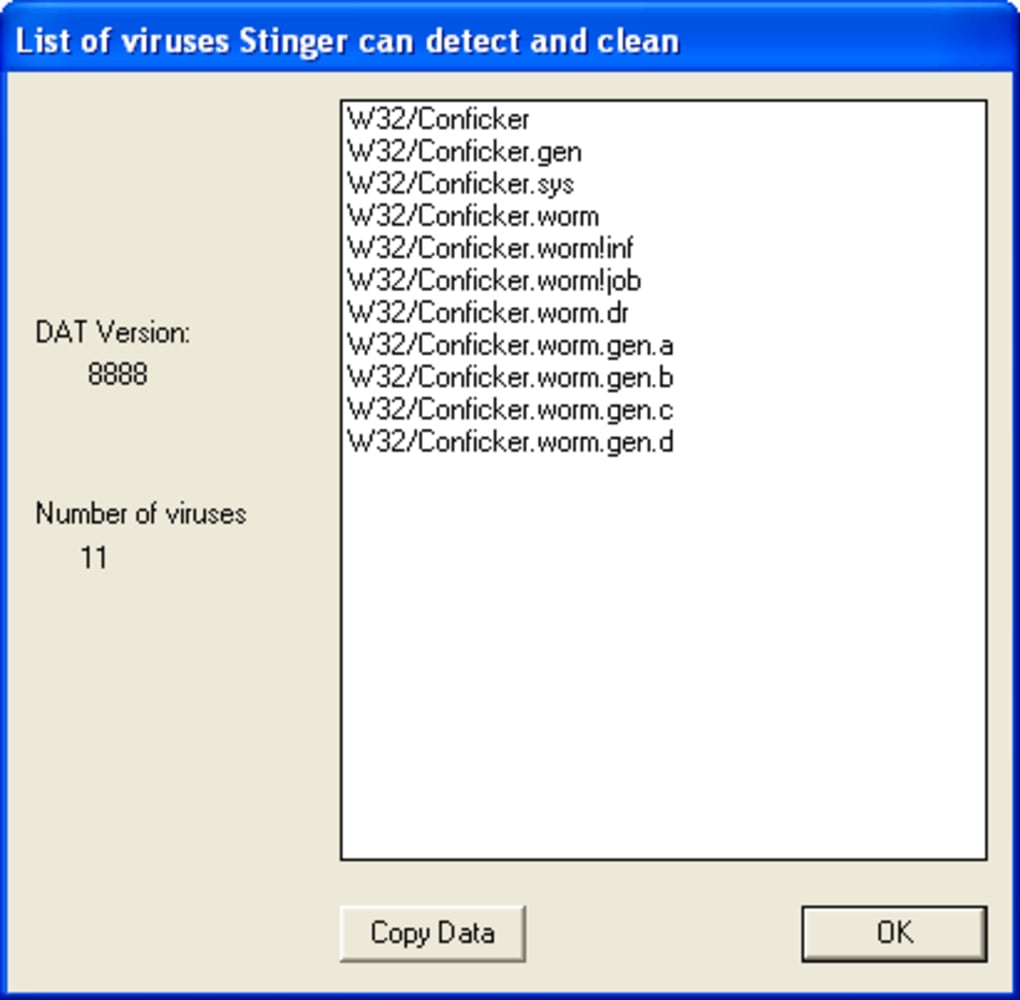
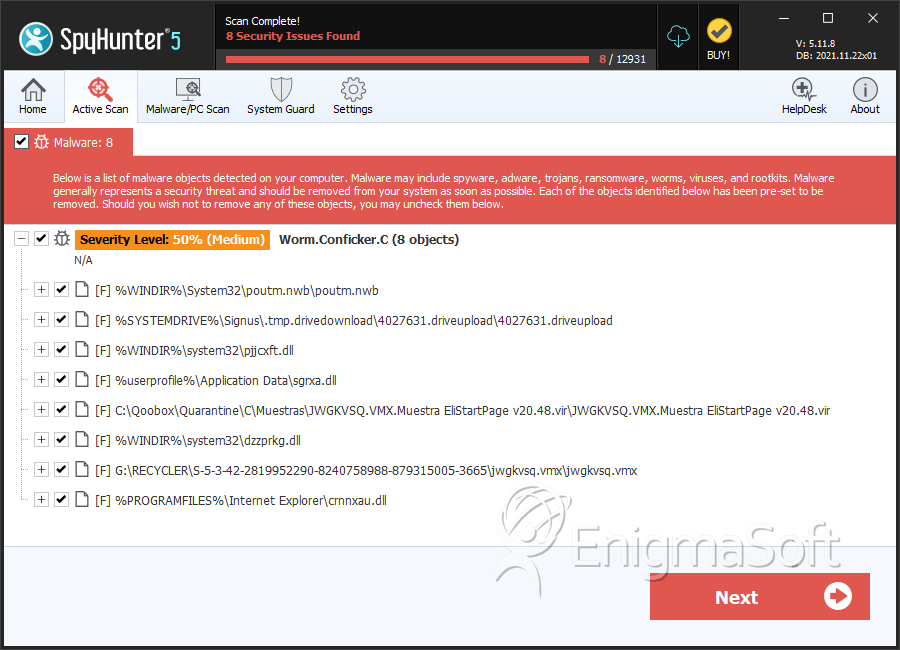
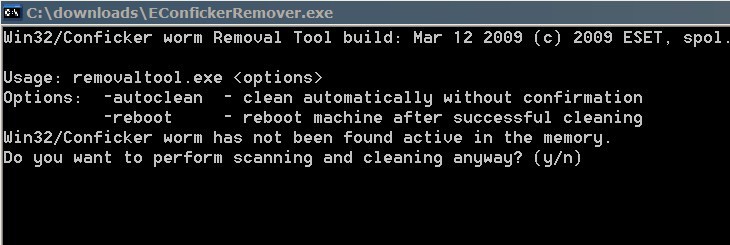
Download and install wireshark on a computer that is constantly getting dropped on by a conficker infected computer. Until recently, there were only two ways to detect conficker, which included monitoring outbound network connections for individual computers, or target scanning each. Carry out a full scan of your computer using panda antivirus, after checking.
| check 1 (port 44329/tcp): Start the logging within wireshark. It requires that “probe services on every port” be enabled.
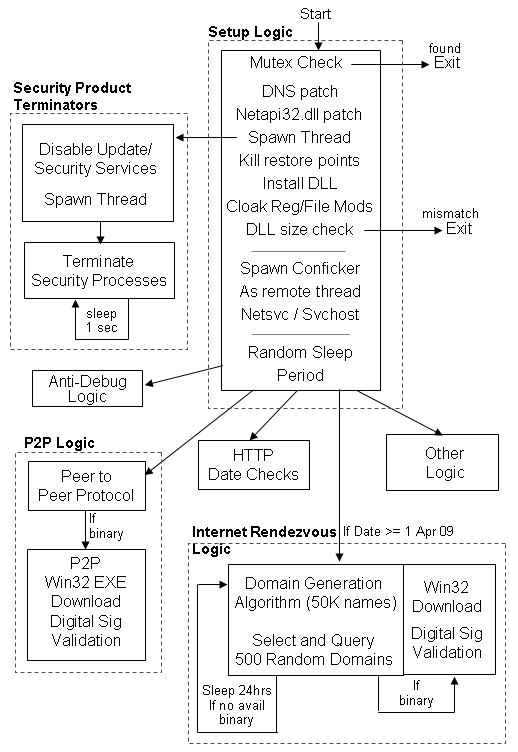
National transportation safety board officials speak during a 2019 news conference. Account lockout policies being reset automatically. This family of worms can disable several important windows services and security products.
Felix and i had a discussion with dan kaminsky about the. 5 hours agocalifornia crash that killed 9 spurs call for new cars to detect drunk drivers. In practice, once a computer gets infected, the hacker.
In the nessus scan policy. Microsoft security software detects and removes this threat. Malware like zeus, conficker and many others use dgas (domain generation algorithms) to build resilient c2 servers.







/cloudfront-us-east-1.images.arcpublishing.com/gray/H625APTEBJCF7C5NR4PHG25M7A.jpg)